In today’s digital-first world, organizations face increasingly complex cybersecurity threats. Traditional security models that relied on firewalls and a “trust but verify” approach are no longer sufficient. Remote work, cloud adoption, and the explosion of connected devices have made networks more porous than ever. This is where zero trust network access (ZTNA) comes into play—a modern framework designed to secure data and applications in an environment where the perimeter has all but disappeared.
This article explores what zero trust network access is, why it matters, and how your organization can implement it effectively.
What is Zero Trust Network Access?
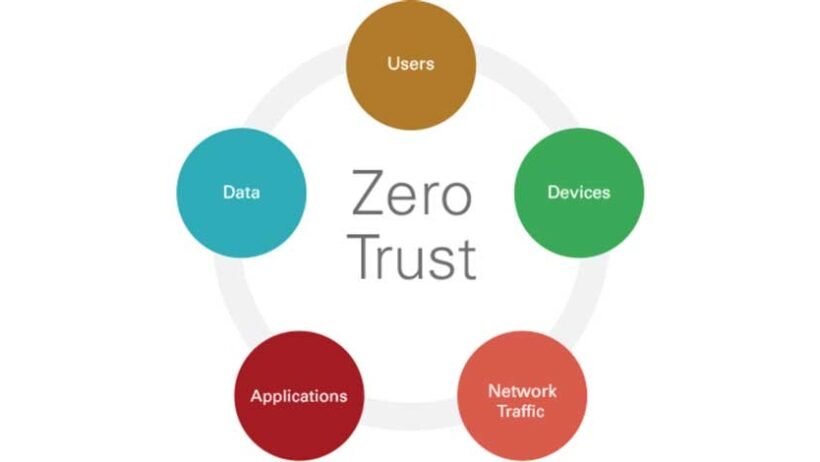
At its core, zero trust network access is a security framework based on the principle of “never trust, always verify.” Unlike traditional security models that assume users inside the corporate network can be trusted, ZTNA assumes no user or device should be inherently trusted—whether they are inside or outside the network.
With ZTNA, every access request is treated as potentially malicious. Verification is required before granting access, and access is limited only to the specific resources the user needs. This minimizes the attack surface and reduces the potential impact of compromised credentials or insider threats.
Key Characteristics of ZTNA
- Identity-Centric: Every user and device must authenticate and prove their identity.
- Least-Privilege Access: Users are granted only the minimum level of access required.
- Continuous Verification: Trust is evaluated at every step, not just at login.
- Application-Level Access: Instead of broad network access, ZTNA provides secure, granular access to specific applications.
Why Zero Trust Network Access Matters
The growing complexity of cyber threats and business operations makes ZTNA critical for modern enterprises.
- Rise of Remote and Hybrid Work
With employees working from home, coffee shops, or anywhere in the world, the traditional network perimeter has dissolved. ZTNA ensures secure access regardless of location.
- Cloud Adoption
Applications and data are increasingly hosted in public or hybrid clouds. ZTNA integrates seamlessly with these environments, unlike traditional VPNs that were designed for on-premises systems.
- Insider Threats
Not all risks come from outside. Malicious insiders—or even well-intentioned employees making mistakes—can pose risks. By enforcing least-privilege access, ZTNA reduces exposure.
- Regulatory Compliance
ZTNA can help meet compliance requirements for frameworks such as HIPAA, GDPR, and PCI DSS by ensuring strict control over who accesses sensitive data.
ZTNA vs. Traditional VPNs
A common question organizations ask is: how does zero trust network access differ from a Virtual Private Network (VPN)?
- VPNsextend the corporate network perimeter to remote users. Once connected, users often have broad access.
- ZTNA, on the other hand, connects users only to the specific applications they need, not the entire network.
This distinction makes ZTNA more secure, scalable, and better suited for cloud and hybrid environments.
Core Components of a Zero Trust Network Access Strategy
Implementing ZTNA is not a single product purchase but a strategic shift. Here are the core components:
- Strong Identity and Access Management (IAM)
- Use multi-factor authentication (MFA).
- Employ single sign-on (SSO) for a streamlined experience.
- Leverage identity providers (IdPs) to centralize authentication.
- Device Security and Posture Checks
- Ensure devices are secure, updated, and meet organizational policies before allowing access.
- Integrate with endpoint detection and response (EDR) solutions.
- Microsegmentation
- Break down the network into smaller, isolated segments.
- Grant access only to the specific resources users or devices require.
- Continuous Monitoring and Analytics
- Monitor user behavior and network activity in real-time.
- Use machine learning or AI-driven analytics to detect anomalies.
- Policy Enforcement
- Automate access decisions with context-aware policies.
- Base access not only on identity, but also device health, user location, and behavior.
Steps to Implement Zero Trust Network Access
Transitioning to ZTNA requires careful planning. Below are the steps to guide the process:
Step 1: Assess Current Infrastructure
Conduct a thorough audit of your existing network, applications, and access methods. Identify vulnerabilities and determine which systems will benefit most from ZTNA.
Step 2: Define User Groups and Resources
Map out your user base (employees, contractors, partners) and identify critical resources. This will help in setting up least-privilege access policies.
Step 3: Deploy Identity and Access Solutions
Adopt an IAM solution with MFA, SSO, and centralized authentication to establish a strong foundation.
Step 4: Implement Microsegmentation
Segment applications and networks so users can only access what they need. This contains potential breaches and limits lateral movement.
Step 5: Enforce Security Policies
Establish policies based on contextual factors like device type, location, and time of access. Automate these policies where possible.
Step 6: Monitor and Optimize
ZTNA is not a set-and-forget model. Continuously monitor traffic, access requests, and user behavior. Adjust policies as threats evolve.
Common Challenges in Implementing ZTNA
- Legacy Systems Compatibility
Older applications may not support modern authentication protocols, requiring workarounds or gradual migration.
- User Experience Concerns
If not implemented carefully, ZTNA can create friction for users. Balancing security with convenience is key.
- Cost and Complexity
Shifting from a perimeter-based model to ZTNA requires investment in tools, training, and possibly new infrastructure.
Best Practices for Success
- Start Small: Pilot ZTNA with a specific group of users or applications before rolling it out enterprise-wide.
- Educate Employees: Ensure staff understand new authentication processes and why they are important.
- Integrate with Existing Tools: Leverage your current security stack, such as SIEM, EDR, and cloud security tools.
- Adopt a Phased Approach: Gradually transition applications and resources to ZTNA to minimize disruption.
- Regularly Review Policies: Conduct periodic reviews to ensure access rules remain aligned with organizational needs.
The Future of Zero Trust Network Access
As organizations continue to embrace cloud services, edge computing, and IoT, ZTNA will only become more critical. Gartner predicts that by 2025, at least 70% of new remote access deployments will be served by ZTNA rather than VPNs.
Additionally, advancements in AI-driven threat detection and adaptive access policies will make zero trust network access smarter and more seamless for users.
Conclusion
Zero trust network access is more than just a cybersecurity buzzword—it is a necessary evolution of how organizations secure their data and systems in an increasingly borderless world. By replacing implicit trust with continuous verification, ZTNA reduces risks, improves compliance, and provides a more secure framework for remote and hybrid work.
While the transition requires careful planning and investment, the benefits far outweigh the challenges. Organizations that adopt ZTNA today will be better positioned to defend against tomorrow’s threats.